Gareth Simpson/Flickr.com
CC-By 2.0
What Is a Security Key for WiFi?
Previously, in our article on “What Is a WiFi Adapter & How Does It Work?”, we vowed to later resume our rant on wireless security protocols. Since we at the IAG strive to keep our word, today’s outing delves into a security key for WiFi. You’ll learn how to keep hackers from encroaching on your home WLAN and safeguard precious WiFi bandwidth for your home devices.
Security and Cryptography
For centuries, people have secured their possessions with locks and keys. Today, in addition to mechanical devices unfastened with metal blades and bows, we also have electronic devices opened by keycards, RFID cards and biometric recognition.
Back in the “daze” of yore, information was secured by encryption—the transformation of comprehensible data into apparent babble. In the 21st-century, cryptography methods using sophisticated algorithms now safeguard sensitive information.
“WiFi” (i.e., IEEE 802.11 standards) uses radio waves. If wireless-capable, your computing device (PC, laptop, tablet, phone) both transmits and receives data across either (or both) 2.4 GHz and 5 GHz frequencies. IEEE 802.11 is an “open” broadcast technology; anyone with compatible gear can access these frequencies.
Hence, when you send or receive info between a device (“client”) and a wireless router (“access point”) using WiFi radio frequencies, your personal data and computer files can surreptitiously be intercepted by rogue devices. So, if using WiFi in hotspots, sensible users employ VPN encryption for their data, protecting it from exploitation by black hats.
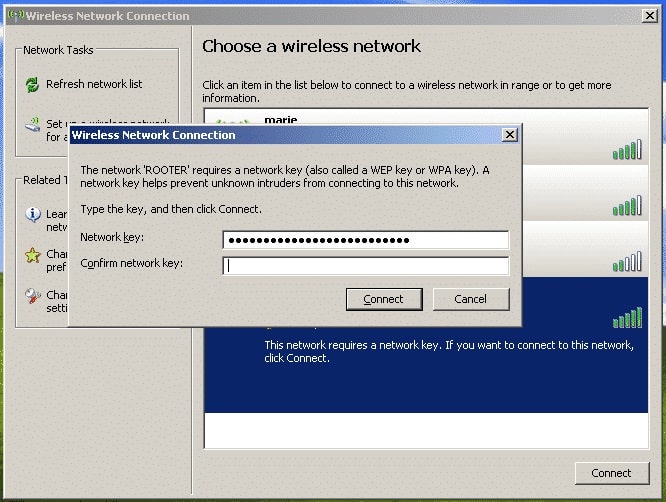
When availing home WiFi, cybersecurity is just as important. Hotspots are meant for public use; your home WiFi is strictly for your family’s devices. While VPNs are typically deployed when using public WiFi, most folks use wireless network keys between a device and wireless router to prevent unauthorized access on their home WLANs.
For sure, the following admonition is a case of “the blinding obvious,” but if your home WLAN is “unsecured,” SECURE IT! An unsecured WLAN exposes your family’s sensitive and private data (banking, SSNs, etc.) to hackers.
Moreover, you also potentially allow unauthorized users to carve out part of your WiFi data pipe (which causes network interference). You probably wouldn’t pay for your neighbors’ utilities such as electric, gas or water, so why would you give them free WiFi?
The WiFi Data Pipe
The point made above merits elaboration. Twenty years ago, when 802.11b and 2.4 GHz devices ruled the wireless roost, WiFi was not the ubiquitous presence that it is today.
Now, with the advent of IoT and the proliferation of home wireless devices, WiFi congestion, interference and intermittent connectivity are endemic to 2.4 GHz frequencies. It’s one reason why the Wi-Fi Alliance developed 802.11n and 802.11ac standards; to take advantage of comparatively unencumbered 5 GHz airwaves.
Even with 5 GHz, WiFi data pipes are still congested—and getting more crowded. Engineer and Ignition Design Labs CEO Terry Ngo explains, “Homes inhabited by more than 80% of the U.S. and 50% of the worldwide population are in urban areas where WiFi connections are steadily getting worse.”
Ngo adds, “Not only is every house on your block likely to have a router but quite a few will have more than one, and many communities are also served by public WiFi networks. Second, increased demand for speed demands wider virtual lanes on the WiFi highway, which means there will be fewer of them. And finally, cellular operators are dumping traffic into the WiFi spectrum.”
When two separate WiFi transmissions collide, “all devices go quiet and then try to ‘talk’ again later,” Ngo stated, using language tech laity can readily grasp. “(This) time delay (is) known as ‘backoff.’ With more collisions, the backoff increases and WiFi becomes slower and less reliable.”
Ngo concludes, “WiFi has become a victim of its own success.” But you can provide some measure of protection to your home’s data pipe by establishing network security keys for your WLAN. While you can’t segregate WiFi frequencies for your own exclusive use, you can at least make your neighbors buy their own Internet access and wireless routers.
WiFi Security Keys
As long as there’s been WiFi, the Wi-Fi Alliance—the shepherd of IEEE standards—has secured it with cryptographic algorithms. Below are the various encryption standards the Wi-Fi Alliance has released to protect WiFi data transmissions.
Wired Equivalent Privacy (WEP)
The first encryption protocol, used for 802.11a/b/g, was Wired Equivalent Privacy (WEP). A data encryption protocol using a combination of system- and user-generated key values, the original incantation of WEP supported key values of 64 bits in total length. Later versions added longer key combinations to bolster security; these variations had 128, 152 and 256 total bit values.
Note that these keys were not transmitted across a WiFi network; values were stored in the device’s OS registry or wireless network adapter.
Two types of WEP are (were) available; shared key authentication (SKA) and open system authentication (OSA). While both are (were) greatly flawed, the former is (was) the less secure. WEP’s fatal defect was the addition of system-generated 24 bits to the key-value, called an “initialization vector” (IV). It’s easily deciphered using readily available WiFi network analysis tools.
In 2004, the IEEE “deprecated” WEP as a wireless security protocol following the deployment of its successor, WiFi Protected Access (WPA). Demonstrating the porosity of WEP, in 2005 the FBI spent all of 3 minutes to decipher a 128-bit WEP key at an Information Systems Security Association (ISSA) confab in Los Angeles.
In short, don’t use it.
WiFi Protected Access (WPA)
WPA was introduced by the Wi-Fi Alliance in 2003 as a stopgap to the security issues WEP posed. WPA2, a more robust version of WPA, was released in 2004. WPA3 followed in January 2018.
Officially known as IEEE 802.11i-2004, WPA2 differs from WPA by using the Advanced Encryption Standard (AES). This block cipher algorithm, a subset of the Rijndael cipher (created by Belgian cryptographers) was adopted in 2001 by the U.S. National Institute of Standards and Technology (NIST) as a federal government specification for encrypting electronic data.
WPA2 is a Robust Security Network (RSN) with two handshakes: four-way and group key. Other security enhancements include Message Integrity Check to prevent attackers from substituting data packets and Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP). Key lengths can be either 128, 192, 256, 384 or 512 bits.
Developed for home WiFi, WPA2-PSK (pre-shared key) allows for the encryption of data without the use of an enterprise-level authentication server. Instead of providing a router with an encryption key, the user enters a “plain-language” password between 8 and 63 characters. (More on this below).
Relying on Temporal Key Integrity Protocol (TKIP; now deprecated), the password, along with the network SSID, generates unique encryption keys—which constantly change—for each wireless user. Although deprecated in 2012, TKIP and WPA2-PSK are still widely used.
WPA3 improves on its predecessors by introducing Opportunistic Wireless Encryption (OWE). The Wi-Fi Alliance claims that the 802.11-2016 revised standard alleviates security flaws presented by weak passcodes.
Yet, WPA3 has already been compromised. In 2019, researchers found that its “Simultaneous Authentication of Equals” (SAE) handshake contains several vulnerabilities open to hacker exploitation. Manufacturers have already begun releasing patches to address these security flaws.
View this video on WiFi password security from Powercert:
Hashcat
Depending upon who uses it, Hashcat is either a password recovery tool or a means to hack into a wireless router. Discovered by a researcher seeking to crack the latest WPA3 security standard, Hashcat captures and solves WPA and WPA2 passwords.
The Hashcat deciphering process is straightforward. A hacker captures one Extensible Authentication Protocol over LAN (EAPOL) frame after requesting it from a WiFi access point (AP). The hacker then extracts the Pairwise Master Key Identifier (PMKID) from the EAPOL frame, formats the data so Hashcat recognizes it and then runs the process to decipher the password.
Depending upon password complexity, the process may take hours or days or seconds. Hashcat doesn’t require the hacker to be in range of both the user and the AP at the precise moment when the network handshake occurs (i.e., authentication from a user password) and the user connects to the WiFi network.
The easiest and cheapest way to protect WPA and WPA2 WiFi networks against Hashcat is to create a complex, random and lengthy password?not one created by the router. A suggested secure password includes 16 (randomly mixed-case alphanumeric and special) characters.
Coda
If you’re adamant about securing data when online, eschew WiFi totally. An Ethernet local area network (LAN) is hardwired, with access limited to an RJ-45 outlet inside a controlled-access environment. Walls and buildings, of course, don’t necessarily confine WiFi to the environment within.
If you’re truly concerned about data security, here’s a thought to keep you awake at night. Wired keyboards emit electromagnetic frequencies, which can potentially reveal data from keystrokes. That Logitech USB keyboard you bought for your laptop? It’s a security risk.
It’s also been documented that computers emit electromagnetic radiation that leaks data. These “compromising emanations” can even leak plaintext. So, should you see someone wearing a tinfoil hat, look again. The person may be trying to protect data leaking from their Google glasses.