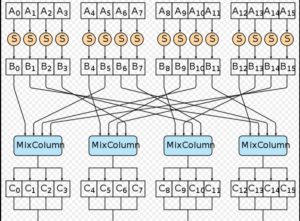
AES Round Function
Source: Yossiea/https://commons.wikimedia.org/wiki/Category:Cryptography#/media/File:Aes_round_function-01.svg
CC BY-SA 4.0
How Virtual Private Network (VPN) encryption works may sound like black arts or rocket science to the uninitiated. Encryption is simply a high-tech version of the decoder ring you and your schoolyard buddies used to keep your all-important messages secret.
Keeping your communications secure is even more imperative now than when you were in rompers. You need to safeguard data about your email account, your financial institution(s) and any number of online destinations from those who would steal your identity, track your activities and drain your bank account. But as long as encryption works, why should you care how?
First, not all VPN encryption is equal. (Nor, for that matter, are VPNs). Some encryption technologies have been around since Windows 95 and, as you might guess, just aren’t as robust as newer, more secure variants. Second, encryption protocols can induce latency in your online connection speeds, an interval you no doubt would like to keep as brief as possible.
Cybersecurity is the raison d’etre for using VPN encryption, viz:
1. Encryption keeps your ISP from throttling your bandwidth since they’re unaware of your online activities.
2. Encryption prevents online spamming and your ISP from mining your personal metadata to sell to advertisers.
3. If you’re downloading torrents (Disclaimer: we don’t advocate violating copyright laws!), encryption maintains your online anonymity, preventing you from potentially being subject to civil fines or criminal prosecution.
4. Should you live in under an authoritarian regime, it keeps you safe from government censors and can even protect you from jail time or worse should you partake in illegal web activity.
So take our nickel tour of today’s VPN encryption protocols and ciphers. You’ll determine what encryption application works best for your specific online needs.
Reading, Writing, Ciphering
A VPN encrypts data between a transmitting computer and the receiving VPN server. A “tunnel” is created; an encryption key using an algorithm informs either end how to encipher/decipher the enclosed data.
First, let’s mention the encryption “handshake” between client and server. It establishes the encryption key used by both ends, concurs upon a VPN protocol, chooses an algorithm and authenticates transmission through the use of digital certificates.
Another part of the handshake process is the secure hash algorithm (SHA), used to authenticate data. A hash calculates a unique signature for each data packet using a “one-way function.” This safeguard protects against “man in the middle” (MITM) attacks that intercept and replace authentic data.
As a rule, VPNs use two different hash algorithms:
-
SHA-1 – relatively faster but susceptible to attack. However, unless you’re the Dread Pirate Roberts, it should be robust enough for your needs.
-
SHA-2 – an improved (and slower) standard, it encompasses a variety of different SHAs, of which the most widely used is SHA-256.
Tales from the “‘Crypt”
Sensitive data has long been encrypted, particularly in diplomacy and war. You may have heard of Enigma, the code used by the German military in World War II to transmit scrambled radio messages to its forces.
VPN encryption uses keys and algorithms to secure data. An encryption key “scrambles” data by using a random sequence of binary digits (e.g., “1” and “0”) aka bits.
An encryption algorithm directs a network’s computer (or server) on how to compute the data when either encrypting or decrypting it. Choose between:
-
Symmetric — the same key is used for all users (or devices) to encrypt and decrypt data.
-
Asymmetric (aka public-key) — two keys are assigned to each user or device to encrypt and decrypt messages. One is a private key for encryption; the other is a matching public key used for decryption.
Symmetric encryption keys connect much faster and are more efficient than asymmetric keys.
Most symmetric keys use either 128-, 192- and 256-bits. Asymmetrical keys may use a much longer string, e.g., 1024-bits.
A cipher using an algorithm encrypts and decrypts data. The cipher of choice is Advanced Encryption Standard (AES), which comes in 128-, 192- and 256-bit symmetric keys. It’s National Institute of Standards and Technology (NIST) certified, NSA approved and used by U. S. government agencies.
Here’s a YouTube vid from Professor Messer detailing the differences between symmetric and asymmetric encryption: https://youtu.be/z2aueocJE8Q
What Does “Protocol” Mean?
Versatile word, that. It can refer to a procedure for how an activity should be performed or rules determining the format and transmission of data, among other nuanced definitions.
While you’re certainly following “protocol” to use a VPN when web browsing, let’s focus here on VPN encryption protocols, i.e., the latter meaning. VPNs need other tools besides encryption to secure data delivery for their clients. Protocols establish frameworks that define transmission of data packet types, encryption standard and the network connection between user and server.
Most VPNs offer a choice of VPN protocols to their clients. How much security do you need? How fast (or slow) are your connection speeds on the web? These two caveats will help you determine which VPN protocol is best for you.
Two predominant authentication applications used by VPNs are Internet Protocol Security (IPSec) and generic routing encapsulation (GRE). Moreover, IPSec incorporates two sub-protocols to instruct a VPN on securing data:
-
encapsulated security payload (ESP), which uses a symmetric key, and
-
authentication header (AH), which hides sensitive data like IP addresses.
VPNs use IPSec with ESP and AH in tunnel mode between the client device and the VPN server. L2PT and IKEv2 protocols are often paired with IPSec to encrypt data packets. Now, let’s take a deeper look at various VPN protocols.
VPN Protocols QED
Most VPNs offer users a choice of protocols from which to choose. Free versions generally do not.
Tech experts and pundits have varied takes on specific VPN protocols. For sure, all protocols have their pros and cons. Three parameters will dictate which protocol(s) you want to use:
1. Application (e.g., browsing, torrents, streaming, etc.)
2. Speed vs. Security
3. Platform (i.e., Windows, iOS, etc.) support
Most VPN clients use one or more of the following protocols:
-
Point-to-Point Tunneling (PTTP)
This technology, native to Windows, is over 20 years old and has no doubt by now been cracked by the U.S. government’s NSA. Uses 40-bit and 128-bit encryption (stay tuned for encryption, addressed below). Supported by all major platforms, including many routers. Fast speeds due to light authentication.
-
Layer 2 Protocol Tunneling (L2PT)/IPSec
L2PT, a protocol developed by Cisco and native to many devices, is also considered vulnerable — but only if you’re attacked by the likes of the NSA. Usually paired with the authentication suite IPSec. Uses 256-bit authentication. Supported by all major platforms including some routers. Speeds are slower than many other protocols. Almost any device that supports PTTP also supports L2TP.
-
Internet Key Exchange, version 2 (IKEv2)
This hybrid developed by both Windows and Cisco is usually configured with IPSec and uses 256-bit authentication. Faster than PPTP, it has low latency when utilized for network applications. Used by two highly regarded VPN providers — TunnelBear and Pure VPN — and others. Supported by all major platforms, it’s especially popular with mobile users.
-
Secure Socket Tunneling Protocol (SSTP)
Another security protocol developed by Microsoft, it’s native to their platforms Vista and higher. Many consider this protocol a safer alternative to L2TP/IPSec. While it offers relatively fast connection speeds if bandwidth is sufficient, the connection itself can be unstable. Uses 256-bit encryption but does not play well with iOS or Mac.
-
OpenVPN
A popular choice worldwide, most users regard this protocol as extremely secure and versatile, sorta fast, stable and offers outstanding speeds over both long-distance (intercontinental) and high-latency connections. Uses 160-bit and 256-bit authentication and supported by all major platforms.
-
Chameleon
Favored by users in China for its data masking capabilities, this protocol also uses 256-bit encryption. Limited to Windows, Android and Mac OS X platforms.
-
SoftEther
Another open-source protocol similar to OpenVPN, SoftEther claims to be 13x faster(!) than OpenVPN. Supported by virtually all platforms and uses 256-bit encryption. Über-safe with many security features for users.
Coda
So, which VPN should you use? The answer lies in the balance between speed, security and connection stability. For what it’s worth, Private Internet Access VPN recommends the following default settings:
-
AES-128 data encryption
-
SHA-1 data authentication
-
RSA-2048 handshake
One final note: if you’re worried about code-source “backdoors,” choose a VPN protocol like OpenVPN or SoftEther. Since both are open-source and not proprietary, you can rest easy knowing that your VPN doesn’t have any hidden backdoors a savvy but unauthorized user can access.