Technology has done wonders for humankind—it’s made our lives easier, more comfortable and more productive. But it can also be used for nefarious reasons. Today’s topic is an example of a technological double-sword: the radio frequency identification (RFID) chip reader aka sensor or, as others refer to it, the Spy Chip reader. While a boon for inventory management, it’s also a threat to personal privacy.
Active and Passive RFID
As we noted in our article on RFID tags last year, there are two varieties of RFID systems: active and passive. There’s also “semi-passive” RFID tags, essentially a passive tag with a battery used “to power other applications with the tag such as sensors.”
Active RFID
In brief, active RFID tags work as either transponders or beacons. In a transponder system, the reader sends a signal to activate the transponder which then replies back to the reader. It’s similar to a passive system but the biggest difference lies in the fact that the active transponder tag is powered by a battery whereas a passive tag is not. One application of this type of Active RFID is the “EZ Pass” used at tollways. Beacons on the other hand emit a data signal every 3-5 seconds without a prompt from a reader. Beacons have found applications in maritime containerized cargo shipping and storage yard asset location systems. As an RFID supplier explains, active RFID systems have certain advantages and disadvantages. Advantages include:
- It can communicate data at distances as far as 300 feet.
- It may have other sensors that can use electricity for power.
- Active tags are capable of operating in rugged environments for years at a time.
- Active tags are battery-powered, and can either transmit constantly or be activated by a signal from the reader.
- The capability of performing diagnostics
- The capability to perform independent monitoring and control
- The capability of initiating communications
Among the disadvantages:
- Cannot function without battery power, limiting the lifetime of the tag.
- Typically much more expensive than passive RFID
- The tag is physically larger, which may limit applications.
- Potential long-term maintenance costs for an active RFID tag if the batteries are replaced.
- Battery outages in an active tag can result in misreads.
Passive RFID
Summarily, passive RFID systems employ chips without an internal power source, using instead an electromagnetic signal generated by an RFID reader. Examples of passive RFIDs are found in supply chain management, smart labels, race timing and file tracking. Advantages of passive RFID tags:
- It functions without a battery; passive RFID tags can have a useful life of twenty years or more.
- It is typically much less expensive to manufacture passive RFID tags.
- It can be much smaller than active RFID tags.
- Passive tags are lighter and are less expensive then the more powerful active tags.
Disadvantages include:
- The tag can be read only at short distances, from a few inches to several feet at most. This limits the device for certain applications.
- It may not be possible to integrate with sensors that use electricity for power.
- The tag remains readable, even after the item to which the tag is attached is no longer being tracked. (See Coda below.)
- Requires a higher-powered reader than active RFID tags
- The orientation of a passive RFID tag must be just right or the reader won’t locate it.
- Passive tags also have difficulty sending data through liquids or metal.
RFID Readers
Per techopedia.com, a RFID reader ” is a device used to gather information from an RFID tag, which is used to track individual objects. Radio waves are used to transfer data from the tag to a reader.” RFID technology, unlike bar codes, needs no line-of sight and items need not be scanned directly. Range varies from a few feet to 100 yards and can discern an individual item amid surrounding tagged objects.
Most RFID tags include an integrated circuit that modulates/demodulated radio signals and an antenna for signal transmission and reception. Frequencies used vary from 125 kHz to that used by Wi-Fi or cellular networks, e.g., 850 MHz and 2.4 GHz. Higher frequency use is limited as they are prone to water absorption.
Readers vary widely in cost. One very affordable model is currently found at Amazon for well under $50. The ID-20 uses a 125 kHZ read frequency, is compatible with EM4001 64-bit RFID tags with 9600 bps, RS 232 and magnetic stripe emulation outputs. More elaborate models, such as the RFID MINI ME, can transform Android devices into EPC Class 1 UHF RFID readers. Using the micro USB port, the MINI ME includes a low level command set API that developers can use to customize UHF RFID software apps. A free demo program is available for download from Google Play or github.
Here is a brief YouTube video demonstrating a reader in tandem with an Android device:
Active readers as a rule use low frequencies—most industrial models prefer the 433 MHz frequency— as low frequencies are better suited for environments affected by metal or water.
Security, Theft & Privacy
RFIDs are great for inventory control and systems management but unfortunately their application has now spread to credit cards, passports and other repositories of sensitive information. Once compromised, they can divulge a trove of data that can be—and is—used for criminal intent.
Check your wallet or your purse. Find a credit card with the words “PayPass” or “Blink”? See a wedge shape with three arcs and a dot at the bottom, the universal symbol for wireless data? That means your card is RFID-enabled and can be cyber-“pickpocketed” without detection by using cheaply and easily available equipment. From the data (which includes card number, expiration date and CVV authentication number) gleaned from a surreptitious encounter, a criminal can encode the victim’s card information onto a blank card by using a card-magnetizing tool. With a Square Credit Card Reader (compatible with iPhone, iPad and Android), a criminal can slowly and methodically drain a victim’s debit account (or amass hundreds of dollars of charges on a credit card account) before the loss is discovered.
The same scenario holds true for U.S. passports. The holder’s data—stored on an RFID chip embedded in the passport—can be easily “skimmed” by anyone with a reader if they’re within a few feet of the passport. Believe it or not, NFC Passport Readers are available for download at Google Play, so should your passport be stolen, someone using this app could quickly access all the information stored on your passport. Security and privacy concerns are valid reasons why everyone should protect their credit cards and passports with an RFID-shielded wallet. A number of these items are available at Amazon, including the Travelon RFID Blocking Tri-Fold Wallet, the D-Armor RFID Wallet Blocking Card Protector and the Leopardd RFID Blocking Leather Wallet for Women.
Coda
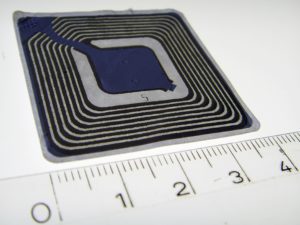
RFID technology can be compared to fire; it has made our lives easier and more enjoyable yet has the potential to wreak great havoc if left unchecked. Part of the problem with RFID technology is that it can be used without our knowledge after its intended use has been fulfilled. Likely your home is filled with “metadata” that can be gleaned from products containing “spy chips”; you’re just unaware of it. Protect your privacy. Should you find an RFID chip (see below) on any item in your home, disable it by severing the antenna from the transponder. (The integrated circuit is the square-shaped object in the center of the chip and the antenna extends from the upper-left hand corner of the integrated circuit to the edge of the chip.)