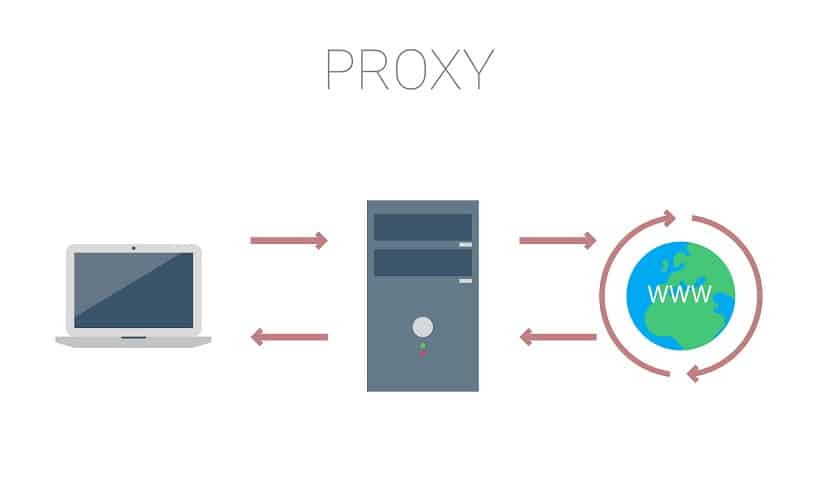
A proxy server has a few different definitions according to the type of proxy you are using. In general though, a proxy server is responsible for allowing you to establish an indirect network connection to other locations and services with your PC or mobile device. Some consider a proxy server to be an application where others define it as a PC or system which provides a service that allows you to establish an indirect connection to another network.
As a whole, a proxy server is capable of filtering traffic and handling client requests so the request can be forwarded to the appropriate server. In plain English this means that a proxy helps you to make a secure connection to another network while keeping your PC and Internet Protocol address anonymous for the majority of the time.
There are many advantages which can be gained by using a proxy server some of which include the ability to surf the web anonymously, increasing the speed of your browsing activity by caching web pages, the ability to offer enhanced security, and blocking questionable websites, to name a few advantages.
There are many different types of proxy servers each of which serves a different purpose. In this article we will discuss a few of the most common proxy servers and the purposes they serve.
SSL Proxy
SSL stands for Secure Sockets Layer and is a protocol which is used to protect your data during transmission. SSL is commonly used on the Internet when you execute a transaction and is symbolized by the padlock icon you typically see next to the URL address in the top of your browser window. It is also symbolized by https as opposed to http.
An SSL proxy server is connected between the client and the server to provide Secure Socket Layer support. SSL basically intervenes in the connection between the sender and the receiver which prevents hackers from attacking the network and intercepting personal or financial information which is being transmitted over the Internet.
FTP Proxy
FTP stands for File Transfer Protocol and is used in many different applications where you are uploading data to a server. A prime example of how FTP works is when you are building a website. In order to make the website visible to the world you must make a connection with the server space you reserved and then upload the website folders to the server to make the site live on the Internet.
An FTP proxy server in advanced mode will offer enhanced security for uploading files to another server. The server typically offers a cache function and encryption methods which make the transmission process secure and safe from hackers. In addition to relaying traffic in a safe environment an FTP server keeps track of all FTP traffic.
HTTP Proxy
An HTTP proxy provides for the caching of web pages and files which allows you to access them faster. Most browsers utilize an HTTP proxy to cache websites you frequently visit so you can quickly access them without having to completely download the page all over again.
When you type in a URL for a website you want to access an HTTP proxy will search for the website address in the cache. If the website address is located it will return the website to you immediately as opposed to you having to wait for it to download.
The downside of an HTTP in some instances is that the cache can build up which slows down your browsing activity. To get around this you must send instructions to clear the cache to speed up your browsing activity. Additionally, an HTTP proxy is capable of filtering content from web pages and reformatting pages to suit the device you are using to access the page.
SOCKS Proxy
SOCKS really stands for SOCKets and is different than a normal proxy since it is considered to be an application. When you compare a SOCKS proxy to an HTTP proxy, the HTTP proxy handles the request you send to access content on the Internet. On the other hand, when you contact a SOCKS proxy server the connection is established through the exchange of messages which establishes the proxy connection.
The connection works through an Internet Protocol (IP) tunnel which also deploys a firewall. The SOCKS proxy requests originate from the firewall using SOCKS protocol and then the network (Internet) communicates with the SOCKS server request as if it were your own machine making the actual request to access a web page.
In order to use a SOCKS proxy your PC must have the capability to handle SOCKS protocol plus it is necessary to operate and maintain a SOCKS server. SOCKS technology was originally developed to access the Internet and its main features are the ability to bypass default routing on an LAN (Local Area Network) or internal network plus, it can provide authentication for protocols that you would otherwise be unable to access.
Anonymous Proxy
An anonymous proxy is just as the name implies and provides you with privacy while you are browsing the Internet. It protects your privacy by hiding your IP (Internet Protocol) address from website owners, eavesdroppers, and other sources that exploit your identity by sending you targeted advertising based on your location or in the case of eavesdroppers, stealing your personal information and listening to your conversations.
An anonymous proxy is also capable of eliminating cookies which track your activity, popup advertisements which can be an annoyance as well as a danger to your PC, and other components that invade your privacy while you are surfing the Internet.
There are a number of anonymous proxy sites online which allow you to protect your identity while you surf the web. Some of them are free and others charge you a fee plus, you also have to be careful which ones you choose to use as some of them are ineffective and can harm your PC. Others provide a secure and safe way to browse the Web.
The quality anonymous proxy servers will provide a SSL (Secure Sockets Layer) tunnel which blocks eavesdroppers. It works similar to the SSL proxy we described earlier. The quality anonymous proxy servers should also support FTP, HTTP, and HTTPS protocols. They also are effective in bypassing your Internet provider to ensure your IP address remains anonymous.